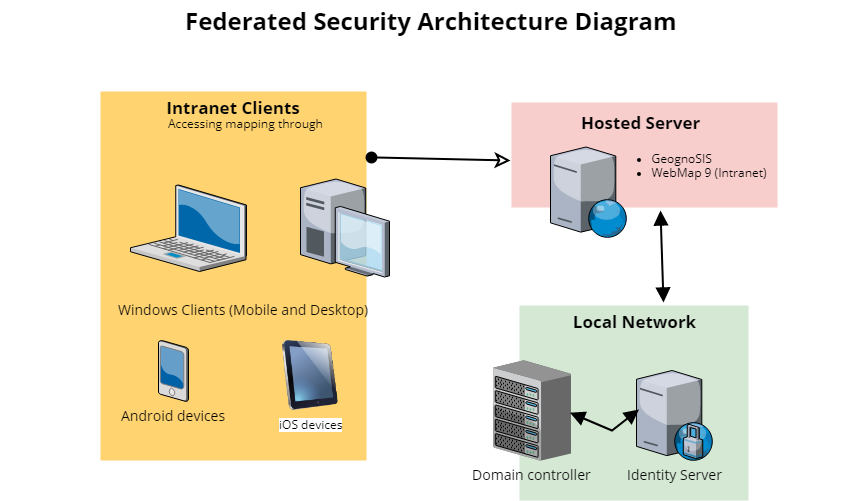
OpenIdConnect Authentication (Federated Authentication)
In this model, only user and group access rights are managed by WebMap; authentication is handled by a 3rd party.
OpenID Connect covers a range of possible authenticators (such as Facebook or Google). The most commonly used option is Microsoft Entra ID which is explained on this page.
See Microsoft Identity Platform  for more details on implementation.
for more details on implementation.
Implementing OpenID Security for Cadcorp SIS WebMap 9.1
- User is presented with an authentication request when WebMap is launched.
- User enters their domain account details and sends the request.
- The request is received by Identity Server, which obtains end-user consent/authorisation from the domain controller.
- Identity Server sends the response back to WebMap as a token.
- WebMap validates the token and authorises the user using its own authorisation database to determine which maps the user can access.
- A server on the customer’s domain for hosting Identity Server. Remote access is required for configuration.
- Identity Server 4.
- CadcorpSIS WebMap
- Harvest of Active Directory users and groups for WebMap Authorisation database.
- Set up an Azure Virtual Machine running Windows Server.
- Ensure the server has a static public IP – this will be needed for the Redirect URIs later.
- Ensure ports 80 and 443 are open on the server (for communication with Identity Server and the Internet) and also port 3389 (to RDP into the VM to install the WebMap and GeognoSIS software)
- Ensure that IIS Manager is installed on the server.
- RDP into the Azure Virtual machine.
- Install GeognoSIS on the VM.
- Install CadcorpSIS WebMap and note the location.
- Inside IIS, turn off all forms of authentication for the instance of WebMap. Refresh IIS to ensure changes have been made.
- RDP into this server.
- Copy IdentityServer files for installation (Cadcorp will supply these) to the location you want your server to be hosted from.
- Open appsettings.json and locate the RedirectUris link. Change this to the location of WebMap (using the public IP address of the Azure instance (eg, ‘http://public IP/website name/’. Note the forward slash at the end of the RedirectUri, this must be present). If multiple sites are being served out by the same instance of Identity Server, separate them with a comma.
-
Open IIS and create a new Application using the path to the folder containing the IdentityServer files.
- For the new application, turn on both Windows & Anonymous Authentication (remember to turn others off) and refresh IIS to ensure changes have been saved.
Note: Identity Server should be installed on a server with .NET Core Runtime 2.0.9 bundle installed on it. The bundle can be downloaded from https://dotnet.microsoft.com/download/dotnet-core/2.0 
Initially, an authenticated user will not have any access to maps. Their map permissions will need to be set after adding their details to the database. The initial user is usually the Administrator.
Identity Server does not directly harvest user and group information from Active Directory.
To populate the WebMap authentication database (which determines who can access different maps) remember to Harvest Users; once user records are imported into the Manager Interface, the GIS administrator can assign permissions to maps (for individual users or groups).
It is possible to enable single sign-on by altering browser settings. Though not required by WebMap, this can provide a smoother user experience.
Chrome
Note: Editing Chrome will automatically change the values in IE.
- Select Settings inside Chrome. Customize and Control (three vertical dots on the address bar) > Settings.
- Go to: Advanced> System > Open Proxy Settings.
- This opens the Internet Properties of IE. Click the Security tab and make sure the Internet zone is selected.
- Now click on Custom Level for security.
- Scroll down to User Authentication > Logon and select the ‘Automatic logon with current user name and password’ radio button’.
- Click OK, then OK again.
- Restart Chrome to apply the changes. (IE will also be updated automatically)
Firefox
Open Firefox’s about:config file and add the following values: (Type about:config in the Location Bar and press Enter to open this file)
- network.negotiate-auth.delegation-uris - http://195.99.130.77
- network.automatic-ntlm-auth.trusted-uris - http://195.99.130.77
- These should both be changed to be the location of the server where IdentityServer is being hosted. Note the lack of forward-slash at the end, this is intentional.
- network.automatic-ntlm-auth.allow-proxies – True
- network.negotiate-auth.allow-proxies – True
Restart Firefox to apply the changes.