How to Add an App for Using the Graph API with WebMap in Azure
Use a dedicated App in Azure to streamline all email activities. The App can be used in conjunction with PowerShell to limit email accounts that can send emails.
TIP: Cadcorp recommends creating separate Apps for authentication and emailing.
- Log in to the Azure portal.
- Click on Microsoft Entra ID.
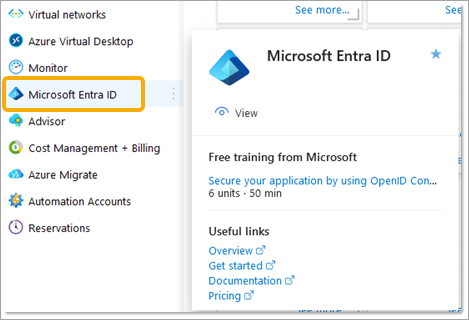
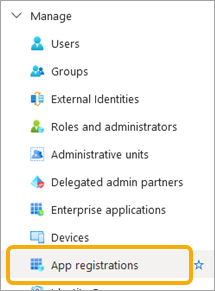
- Select Manage > App Registrations.
- Click New registration.
- Enter a Name to register and application and Register.
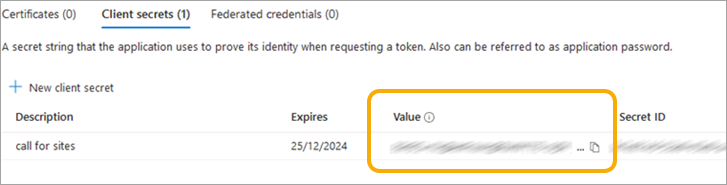
- Inside the App under Manage, click on Certificates & secrets > + New client Secret > Add > Descriptions and Expires value.
- Enter any relevant values and press Add.
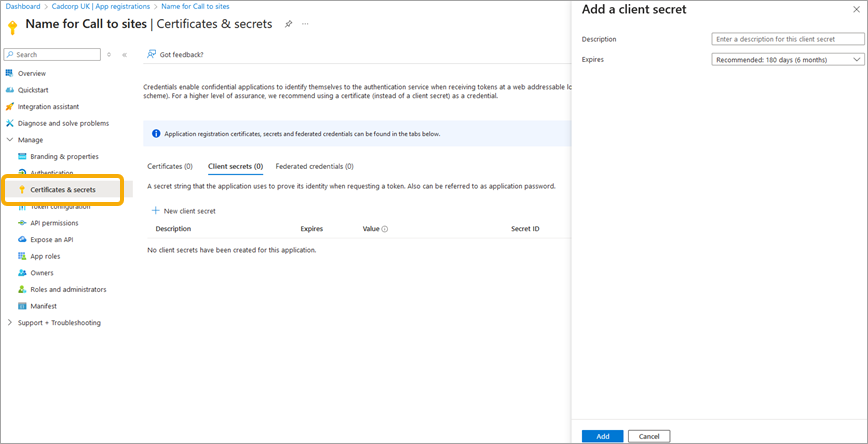
- Make a note of the new Value, this is needed in WebMap.
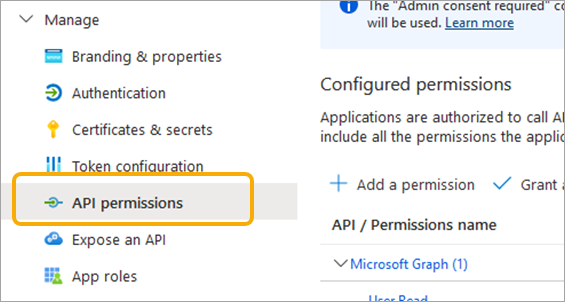
- Select Manage > API permissions > + Add a permission.
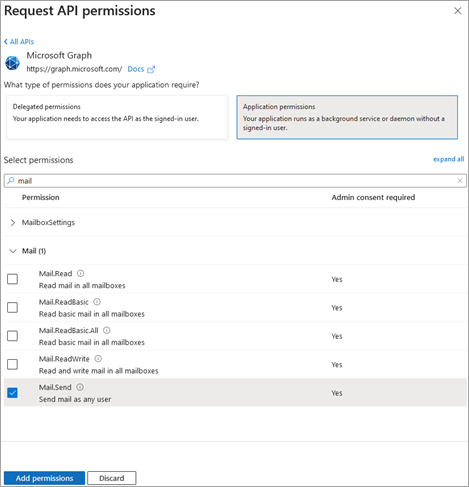
- From the Request API permissions select Microsoft Graph > Delegated permissions > Mail > Mail.Send and click then Add permissions.
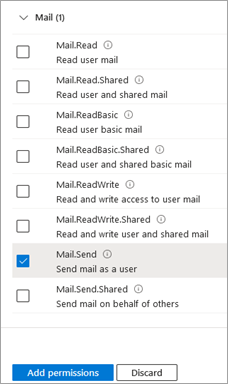
- Click +Add a permission again, select Microsoft Graph > Application permissions > Mail > Mail.Send and click then Add permissions.
- Click Grant admin consent of (company name) by pressing Yes.
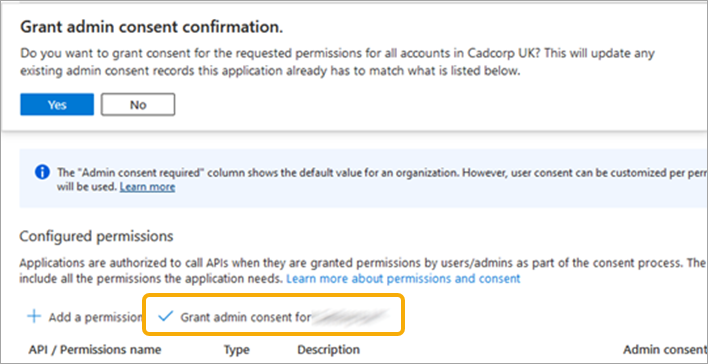
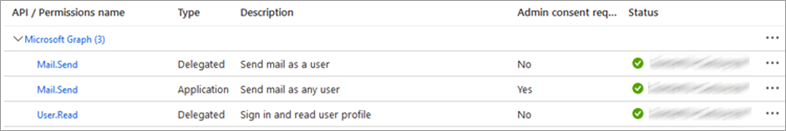
- The configured mail permissions will look like this:
Click on Overview at the top of the List.
WebMap needs:
- Application (client) ID
- Directory (tenant) ID
- Application Secret (value)
- User with a valid email account
Customize email accounts that can send emails using the Graph API
By default, all users with a valid email account can send an email. However the Azure Administrator can restrict this capability to specific email accounts. This is done by using the PowerShell Exchange Online Management module.
Run Windows PowerShell ISE as Administrator. Run the following commands:
Install-Module -Name ExchangeOnlineManagementImport-Module ExchangeOnlineManagementSet-ExecutionPolicy RemoteSignedConnect-ExchangeOnline -UserPrincipalName ****exchange admin user email address****New-DistributionGroup -Name "MyEmailService" -Alias myemailservice -Type securityNew-ApplicationAccessPolicy -AppId ****Application (client) ID from new App registration**** -PolicyScopeGroupId **** myemailservice@(azure domain name) @xxx.onmicrosoft.com, can then add domain to this email account**** -AccessRight RestrictAccess -Description "Restrict this app to members of distribution group MyEmailService."Add-DistributionGroupMember -Identity MyEmailService -Member callforsites@eastherts.gov.uk -Confirm:$false
