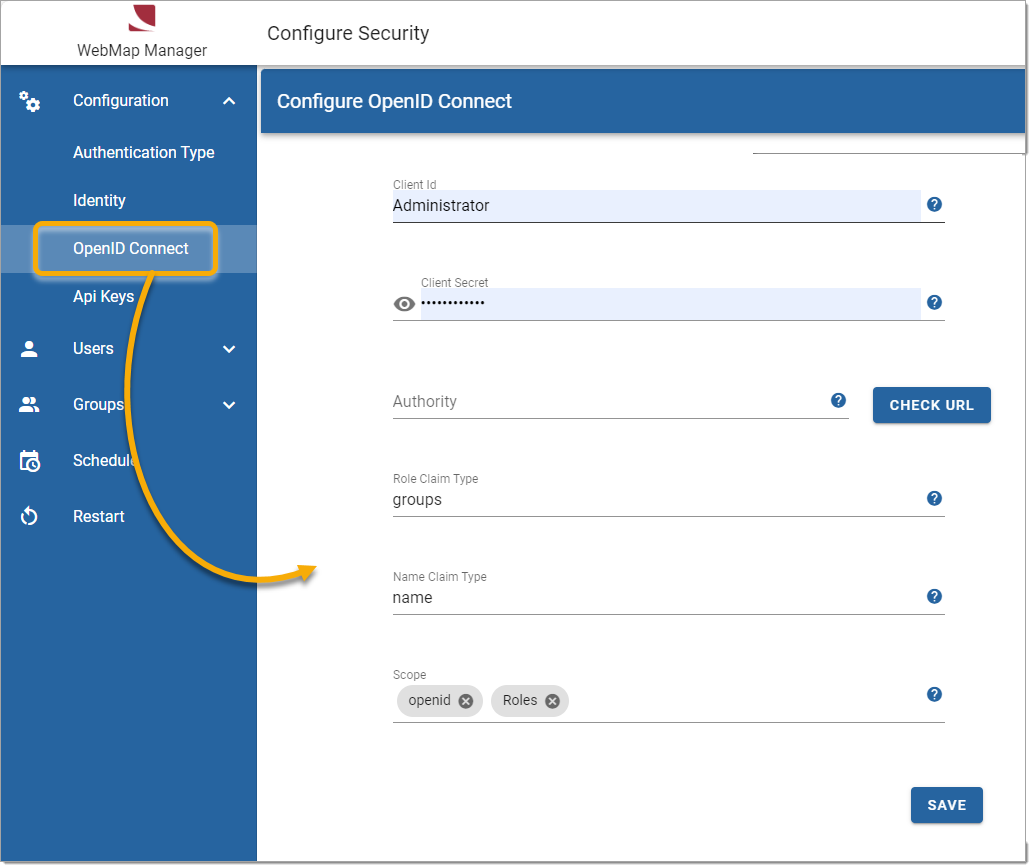
OpenID Connect
Select Configuration > OpendID Connect and edit these fields accordingly. See here for more on OpenID architecture and setup.
|
Client ID |
Sets the client_id parameter on the authentication request |
|
Client Secret |
Sets the client_secret parameter on the authentication request |
| Authority | URL pointing to the Identity Server folder. For eg. https://login.microsoftonline.com/<your tenant ID> |
| Role Claim Type | Sets the claim type in the returned authentication token that WebMap will use to determine role claims. |
| Name Claim Type |
Sets the claim type in the returned authentication token that WebMap will use to determine the user name. For e.g. http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name Name claim types differ from organisation to organisation. To find out the type of claim to use:
|
| Scope | Scope refers to the extent of resources assigned to a particular access level. |
Using dynamic groups with Azure authentication
Dynamic group membership adds and removes group members automatically using membership rules based on member attributes.
If a dynamic group has been granted access to WebMap 9.1 but users in the group are unable to gain entry to the map, edit the configuration as follows.
- In the Azure Portal, navigate to the token configuration section of your app and open Groups Claim .
- Disable Directory Roles.
- Enable Emits groups as role claims.
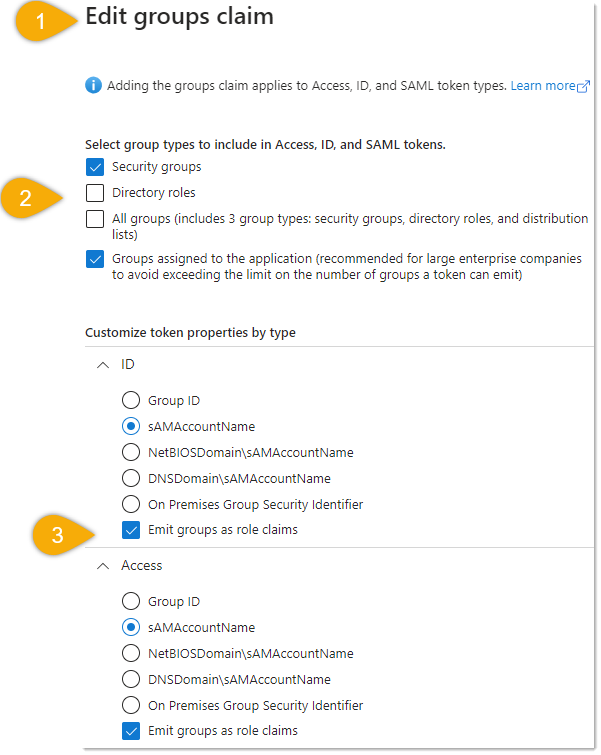
- In WebMap Manager’s OpenID Connect configuration, update the role claim type to match the claim type specified in all claims.